What You Need To Know About Tor And The Hackers Targeting It

There are a lot of tools online that claim to offer you total privacy. But when dealing with something like Internet anonymity, it’s hard to be sure.
One that’s widely agreed to be among the best available is Tor. If used correctly, the Tor browser and network cloaks online activity in anonymity; your online traffic isn’t traceable back to you. It’s less about keeping credit card numbers secure and more about allowing you to browse the web and communicate with others without revealing who and where you are.
But Tor was attacked on Friday. The hacker group known as Lizard Squad — or at least a Twitter account claiming to be involved with the collective — said that it was going after Tor. According to Tor, which has confirmed the attack, but not the perpetrator, there should be no effects on anonymity or performance. But some experts have speculated that the hackers could track the network’s users.
This comes one day after the hackers took credit for shutting down the PlayStation Network and Xbox Live. The group has claimed responsibility for numerous hacking attacks. It’s not entirely clear if Lizard Squad is actually behind all of these hacks, or if the Tor attack is actually being carried out by the group.
Tor’s developers openly admit it isn’t bulletproof. But nothing is. A report from Wired earlier this month, for example, said the FBI used a hacking app called Metasploit to successfully identify users hiding behind Tor in 2012, and “there’s evidence the FBI’s anti-Tor capabilities have been rapidly advancing.”
Just last week, Tor heard word of a possible attack to disable the network by seizing “specialized servers,” according to a post on Tor’s website. Whether the new attack is connected to these concerns is unclear.
“Any tool that says they are 100% secure all the time, they are not being accurate,” Tor’s development director Karen Reilly said in an interview earlier this month.
What exactly is Tor?
Tor — first called “The Onion Network,” because of its security layers — refers to two things: a network designed to help users keep their online activity anonymous, and software that’s built to automatically run data through Tor’s network. It was originally designed by the U.S. Naval Research Laboratory with the armed forces in mind to protect government correspondence.
Ironically, now many people are worried about governments monitoring what they do online. Tor is now available for everyone, from experts to regular Internet users, to download for free. It works by passing information through relay nodes in different locations.
“It’s basically like using a courier system,” Reilly said. “Your message is an envelope inside of an envelope inside an envelope inside an envelope.”
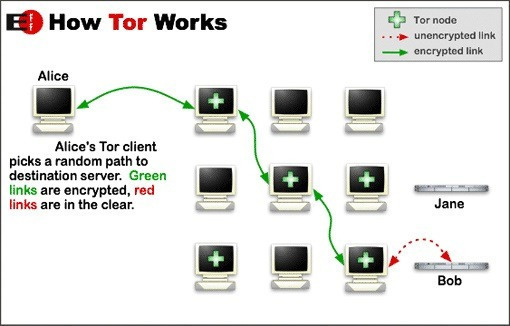
Think of it, as Tor’s website describes, as a driver taking a deliberately twisty, complex, roundabout route to lose someone who’s tailing them.
What kind of information does Tor hide?
Tor obscures your IP address, which is a direct identifier of your digital presence. It makes the origins of Internet traffic anonymous — the traffic itself exists, but it’s encrypted inside the network. Once it goes through a Tor exit node, it’s tough to tell who or where it came from.
What Tor is trying to do is send your Internet traffic through several proxies. It’s encrypted in multiple layers.
In the most basic terms, Tor hides your location.
Does this mean it’s now unsafe to use Tor?
Tor claims that the network is not compromised.
“This looks like a regular attempt at a Sybil attack: the attackers have signed up many new relays in hopes of becoming a large fraction of the network,” according to a Tor statement. “But even though they are running thousands of new relays, their relays currently make up less than 1% of the Tor network by capacity. We are working now to remove these relays from the network before they become a threat, and we don’t expect any anonymity or performance effects based on what we’ve seen so far.”
Security specialists first noticed something strange was happening on Tor on Friday.
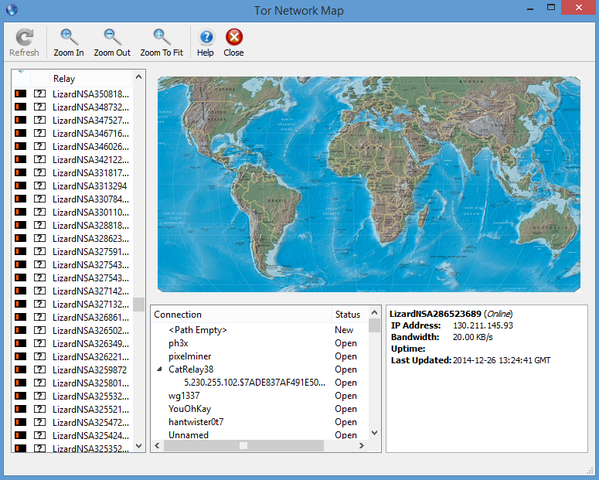
The hackers claiming to be part of Lizard Squad are apparently starting their own collection of nodes. Some have already speculated that this could allow Lizard Squad to track Tor’s users, thereby spoiling any sort of anonymity.
On Twitter, the group said that it was going after Tor because it is only used by evildoers.
But Anonymous, a thinly defined group of “hacktivists” that strongly oppose Internet censorship and known for donning Guy Fawkes masks, stood behind Tor after the attack.
“Someone who claims to be a part of Lizard Squad has set up a large number of Tor relays. That’s it,” Runa A. Sandvik, an advocate with Tor, told Gizmodo.
Cybersecurity journalist and former Washington Post reporter Brian Krebs wrote a takedown of Lizard Squad on Friday on his website after the group claimed responsibility for taking down the PlayStation Network and Xbox Live.
“Many of those associated with LizardSquad are wannabe hackers with zero skill and a desire to be connected to something interesting and fun,” Krebs wrote.
A large number of people who are part of Lizard Squad are minors, Krebs wrote, and the federal government doesn’t “really know what do with underage felons.” The attack methods employed by the hackers are in no way sophisticated.
Is Tor legal?
The short answer is yes.
Obviously, Tor can be used for sinister reasons, like anonymous threats of violence. That action is illegal. Using Tor is not.
Tor and the Electronic Frontier Foundation claim that nobody has ever been sued for running Tor in the U.S.
“To our knowledge, no one has ever been prosecuted or threatened with prosecution for using Tor,” Nate Cardozo, a staff attorney at the Electronic Frontier Foundation said. His organization advocates for civil rights as they relate to modern technology.
Things could get legally dicey for people who run what are called exit nodes for Tor. These act as the end point for Internet traffic that travels through Tor’s relay nodes. That’s far from a beginner’s game, however, so it’s not something most Tor users have to worry about at all.
Despite Lizard Squad’s proclamations about Tor’s user base, the network is often used by journalists and political activists in countries with heavy Internet regulation.
Tor has been involved in some high-profile situations, such as when Edward Snowden leaked top-secret information to journalists Laura Poitras and Glenn Greenwald.












 © 2024
© 2024
0 comments